Networking plays a critical role in Kubernetes, enabling communication between pods, services, and external entities. In a Kubernetes cluster, various network components work together to ensure that traffic flows smoothly within the cluster and to the outside world. Understanding how Kubernetes networking functions is essential for diagnosing and resolving networking issues effectively.
Kubernetes Networking Overview
Kubernetes follows a flat networking model, meaning all pods can communicate with each other without Network Address Translation (NAT). This allows each pod to have its unique IP address, which simplifies network communication. Key components of Kubernetes networking include:
- Pods: Each pod gets an IP address, enabling communication with other pods.
- Services: Services provide stable IP addresses for accessing a group of pods, acting as load balancers within the cluster.
- CNI Plugins: Container Network Interface (CNI) plugins are used to configure the network and assign IP addresses to pods.
- Ingress: Ingress allows external traffic to access services inside the cluster, acting as an entry point.
How Kubernetes Networking Works
- Pod-to-Pod Communication: Each pod gets an IP from a pool defined by the CNI plugin. Pods communicate with each other using their assigned IP addresses.
- Service Discovery: Kubernetes services route traffic to a group of pods. When a request is sent to a service, it is forwarded to one of the backend pods.
- External Access: Ingress controllers manage external access, routing traffic from outside the cluster to internal services.
Here’s a simplified diagram showing the flow of traffic between pods, services, and external clients in Kubernetes networking:
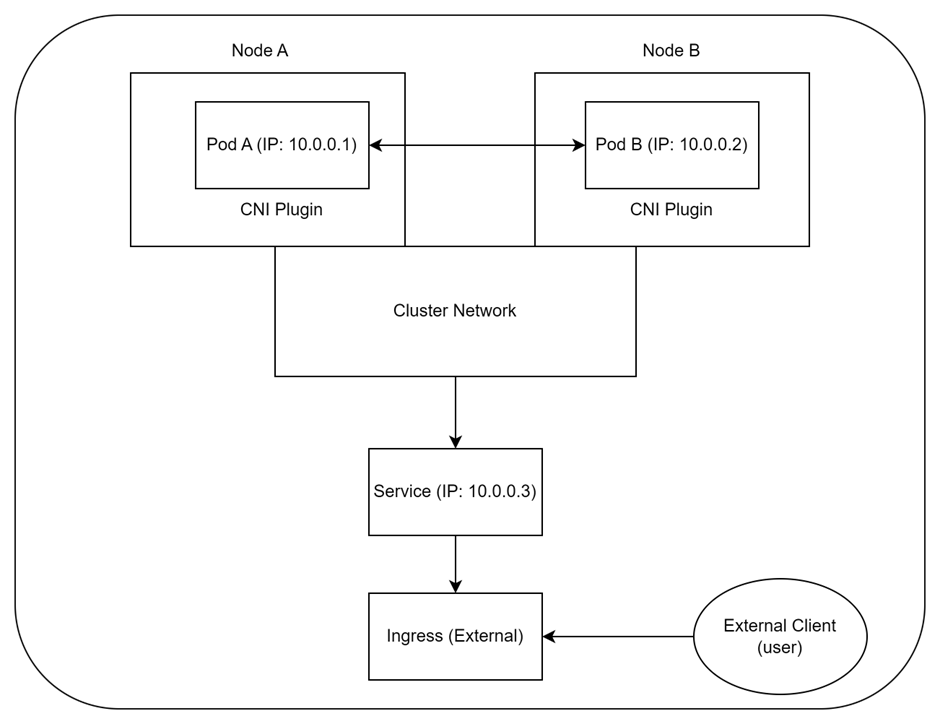
Explanation:
- Node 1 and Node 2: Represent physical or virtual machines running in the Kubernetes cluster.
- Pod A and Pod B: Pods running on different nodes, each with a unique IP address assigned by the CNI plugin.
- CNI Plugin: Handles networking between the nodes, ensuring that pods can communicate with each other.
- Service: Provides a stable IP address to access multiple pods behind it (in this case, routing traffic to Pod A and B).
- Ingress: Acts as an entry point for external traffic, directing it to the correct service.
- External Client: Represents an external user or system requesting the service inside the cluster.
For more detailed information about kubernetes networking refer the official documentation here.
Example: Checking Pod IP Address and Network Information
To check the network configuration of a pod, use:
root@rke2-server1:~# kubectl get pod <pod-name> -o wideThis command shows the IP address assigned to the pod. You can also inspect the CNI plugin and networking details by running:
root@rke2-server1:~# kubectl describe pod <pod-name>Common Issues
CNI Plugin Problems
CNI plugins manage the networking within Kubernetes. Misconfigurations or failures in the CNI can lead to networking issues such as pods not communicating or not receiving IP addresses. Here are some common issues and how to troubleshoot them:
- Misconfigured CNI Plugin: A common issue is misconfiguration in the CNI plugin settings. Checking the logs of the CNI plugin can provide insights into errors:
root@rke2-server1:~# journalctl -u kubelet | grep CNIIf errors are found, the issue can be resolved by verifying and correcting the configuration in the CNI plugin YAML files.
- IP Address Exhaustion: Pods may fail to get IP addresses if the IP range is exhausted. This can be checked and fixed by increasing the available IP range in the CNI configuration.
- CNI Plugin Not Starting: The CNI plugin may not be running correctly, resulting in network failures. This can be diagnosed by checking the status of the CNI daemon.
root@rke2-server1:~# kubectl get daemonset -n kube-system
NAME DESIRED CURRENT READY UP-TO-DATE AVAILABLE NODE SELECTOR AGE
rke2-canal 3 3 3 3 3 kubernetes.io/os=linux 6d
rke2-ingress-nginx-controller 3 3 3 3 3 kubernetes.io/os=linux 6dIf the CNI plugin is not running, redeploying the plugin can resolve the issue.
Ingress Controller Troubleshooting
Ingress controllers manage the routing of external traffic into the cluster. Problems with ingress can cause services to be inaccessible from outside the cluster.
- Misconfigured Ingress Rules: Incorrect ingress rules may block external traffic. These can be reviewed using:
root@rke2-server1:~# kubectl describe ingress <ingress-name>Adjusting the rules to correctly route traffic often resolves the issue.
- SSL Certificate Issues: Expired or misconfigured SSL certificates can prevent secure connections. To verify the status of SSL certificates, inspect the ingress configuration. If the certificate has expired, renewing or updating the certificate can fix the problem.
- Load Balancer Misconfigurations: External load balancers may not correctly direct traffic to the ingress controller. You can verify the load balancer status using:
root@rke2-server1:~# kubectl get svc -n ingress-nginxLogs from the load balancer and ingress controller can provide more details about the root cause of the issue.
Tools & Techniques
Several networking tools can be used to troubleshoot Kubernetes network problems:
- Traceroute: Traceroute helps trace the path packets take between pods or from external systems to the cluster. It is useful in identifying where a connection is breaking down.
Example command to use traceroute within a pod:
root@rke2-server1:~# kubectl exec -it <pod-name> -- traceroute <target-pod-ip>- Ping: This tool checks connectivity between pods or between pods and external systems. A successful ping confirms that a connection exists.
Example command to ping another pod:
root@rke2-server1:~# kubectl exec -it <pod-name> -- ping <target-pod-ip>- kubectl: Kubernetes built-in tool
kubectlis valuable for debugging. Usingkubectl execto run commands inside a pod, orkubectl describeto get detailed information about resources, provides insights into networking issues.
Example of checking network status inside a pod:
root@rke2-server1:~# kubectl exec -it <pod-name> -- ifconfigReliable networking is essential for the smooth operation of Kubernetes clusters. Common networking issues like CNI plugin failures or ingress misconfigurations can often be diagnosed and resolved using the right tools and techniques. By understanding how Kubernetes networking functions, regularly monitoring network components, and using the appropriate troubleshooting methods, administrators can ensure that networking issues are resolved quickly and efficiently. Maintaining updated network configurations and employing best practices helps ensure seamless communication within the cluster and with external entities.
For more insights and detailed guides on Kubernetes, be sure to check out my Kubernetes blog for the latest tips and best practices!